According to the most recent survey on the use of technologies that enable access to the Dark...
market
For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with...
When you try to connect to a .onion website, Tor will route your traffic through three or...
Mixer makes it possible to conceal the origin or destination of BTC. Here are some of highlights...
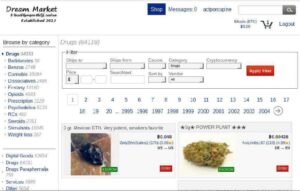
Furthermore, deterring drug users from the darknet could lead to them buying drugs on the streets, which...
However, these domains are not easy to distinguish, and are usually represented in long, often randomly generated...
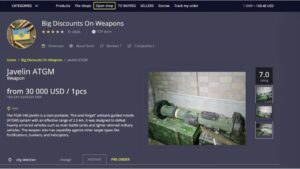
These sites cater to cybercriminals seeking valuable data, such as credit card numbers, login credentials, and personal...
These platforms leverage advanced encryption technologies, decentralized systems, and user-friendly interfaces to ensure seamless transactions. The integration...
I tested it 10+ times, and it always provided me with accurate search results. For example, I...
Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering...