Similarly, White House Market stands out for its focus on privacy, requiring users to employ PGP encryption...
A notable example in the history of such marketplaces is Silk Road, which gained notoriety as one...
The durability of these markets tells us that if policing responses keep following the same playbook, they...
In terms of size, cryptomarkets are currently smaller than other modes of digital drug distribution such as...
Whether you’re new to the dark web or a vet who’s seen it all, you’ll find something...
As large platforms face disruption from law enforcement action, dark web infighting, and an influx of users...
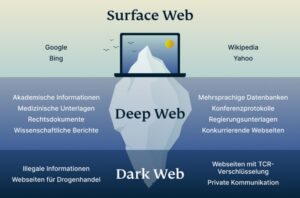
As for Tor and other anonymous browsers that allow access to the Deep Web and the Dark...
This protects vendors from many risks that are prevalent in other forms of drug supply, including undercover...
You don’t have to worry about driving to a dispensary or meeting with a dealer, and you...
Yes, it is not illegal to use the darknet cc market to buy or sell legal goods...