In theory this should make your deep web browsing (as well as your regular web browsing) entirely private from interlopers. However, since your traffic is routed through nodes that you don’t have any control over, you are at the mercy of whoever operates these nodes. Serving is the final step of the process for search engines like Google. This is when it takes a search query from the user, finds the most relevant results in the index, and then serves the resulting web pages back to the user. The terms “deep web” and “dark web” are commonly used interchangeably. Although this is accurate in terms of the underlying technology, there is a slight difference.
Deep Web Entrar De Forma Segura Y Anónima
Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN. Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor. Instead, you need to get the Tor browser to access the dark web. Make sure that when you download the Tor file, it’s from their official website.
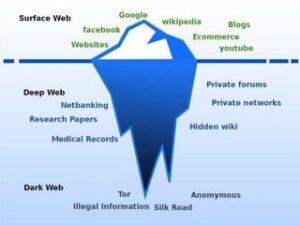
- The Deep Web refers to web data you can’t find using a search engine like Google.
- For example, Google.com and PixelPrivacy.com both belong to the “.com” top-level domain.
- You can look for information on /r/deepweb, /r/TOR, or /r/onions, of which the latter is useful to find hidden wikis and more.
- Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito.
Usa Una VPN
DuckDuckGo is the default search engine inside the Tor browser, and once you turn on the Onionize toggle switch in the search box, you’re able to use it to find dark web links. These typically come with “.onion” after them, rather than something like “.com” as on the standard web. As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman.
Browsing The Dark Web With Tor
The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. Data gleaned from ransomware and data breaches is available on the dark web. Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data. There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes.
Browse Privately
Now, if you want to see what lurks in the dark corners of the Internet but don’t really trust Tor, there are alternatives. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable.
Tudo Sobre O Primeiro Mercado Da Dark Web, O Site Silk Road

As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web. Individual sites on the dark web look much like they do on the regular web, though a lot of them are a bit more rough around the edges. (Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS. While there are other browsers you can use to get on the dark web, Tor is usually recommended as the best for most people in terms of the features it offers and the ease with which anyone can make use of it.
Instead, download Tor, the most secure and user-friendly option for accessing .onion sites. Despite some skepticism about its origins and privacy due to its military development, Tor remains the preferred choice for safe dark web navigation. Now you know how to enter deep web safely, the key differences between deep web vs dark web, and which best deep web browsers to use. Whether for professional or personal use, accessing the deep web responsibly ensures privacy, security, and efficiency.
Dark Web Search Engines
As you might expect, Bitcoin is the top cryptocurrency being used on the Dark Web. Chainalysis says that $790 million worth of cryptocurrencies were used to shop in darknet markets during 2019. While some studies have claimed that illegal Bitcoin activity is as high as 44%. Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware.
- Just remember, if you want to explore the dark web, be very careful.
- NordVPN offers a 30-day, no-risk trial subscription when you sign up on this page.
- Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia.
- Cybersecurity has to also cover everything physically on your computer too—which law enforcement or government authorities might have the right to seize if they come calling.
- The most common way to access the dark web or deep web is by using the Tor network, and doing so is not nearly as complicated as you might think.
Because of this, tracking down the web addresses of deep web sites is a much more manual process. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails. This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. But remember, it’s essential to take all the necessary and important security steps before entering such sites on the dark web.
Advocacy groups are also reaping the advantages of the darknet because, here, the term of censorship is as popular as HTTPS. And finally, we have political outcasts, refugees, and people who want to get in touch with the outside world, being from a totalitarian country that suppresses all means of communication and information. Believe it or not, Zuckerberg’s Facebook has a darknet version. People mostly use it for covert communication, anonymous tips submission, and stuff like that. Well, now it’s time to fire up Tails and do a little bit of tinkering.
Install The Tor Browser
The dark web is used by journalists, whistleblowers, and political activists who need the protections that it offers. Anything you need to do that has to be off the books to some extent, for noble or ignoble reasons, can be done on the dark web. Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. Next step – your request will be transferred to Tor entry nod which in turn transfers to one or more Tor relays. Afterwards, your request will be matched with the appropriate website. Tricky, but effective; that’s why it’s, by far, the best method to access dark web content.

Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Cybersecurity has to also cover everything physically on your computer too—which law enforcement or government authorities might have the right to seize if they come calling. If you want to be untraceable and undetectable, connecting to the dark web via the Tor browser is a major step towards that, but not the only step you’ll need. When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails.
Download Tor Browser to experience real private browsing without tracking, surveillance, or censorship.
The dark web is also a place for scammers to attract vulnerable and unwitting victims. The platform is also used by governmental cyber departments to identify and track potential criminals or offenders. You can never be sure who’s really behind the other end of the line. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.

The users only have access to a fraction of the available data and web pages. Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing. Many people install a VPN as well, but then you’re putting your trust in an additional third party to not track your activities or report them to anyone else. Always remember that the dark web is a people-centric community. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers. There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game.
Content includes non-indexed websites, apps, and resources, which can include protected information such as, online banking, specialized databases, non-linked and password-protected websites, and more. It includes media and archives which cannot be crawled and indexed with current search engine technology. The deep web refers to portions of the internet not indexed by standard search engines. This includes everything from academic databases to medical records, government resources, and confidential corporate documents stored behind login credentials. Aleksandar Kochovski is a cybersecurity writer and editor at Cloudwards, with a rich background in writing, editing and YouTube content creation, focused on making complex online safety topics accessible to all.