To access the purposely hidden part of the internet, you have to use special tools such as the Tor browser. Other specialist browsers like Freenet, ZeroNet, RetroShare, GNUnet, Lokinet, and Tribler are similar to Tor. However, while the internet includes a lot of data we don’t usually see (deep web), the dark web has a reputation for concealing and facilitating criminal activities. The Gray Web, Deep Web, and Dark Web are all valuable sources of threat intelligence, but many organizations limit their information-gathering efforts to the Surface Web. Expanding their reach – through the use of Dark Web monitoring tools – can be invaluable to a corporate cybersecurity and risk management program. If you engage in illegal activities or access illegal content that could implicate you in a criminal offense, you may face serious legal consequences, including fines and imprisonment.

PRIVACY ALERT: Websites You Visit Can Find Out Who You Are
China uses what is known as the “Great Firewall” limit access to popular sites for this exact reason. The risk of being a visitor to this content could lead to being placed on a watchlist or immediate targeting for a jail sentence. All commonly public-facing websites accessed via traditional browsers like Google Chrome, Internet Explorer, and Firefox are contained here. Websites are usually labeled with registry operators like “.com” and “.org” and can be easily located with popular search engines. One study found that only 6.7% of Tor anonymity network daily users — a cohort that comprises mostly dark web users — connect to onion sites used for illicit activity.
The 10 Best Dark Web Browsers In 2025
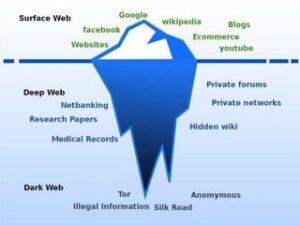
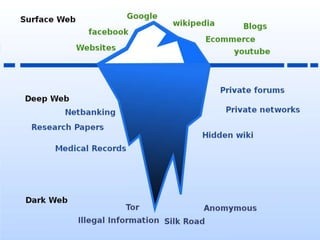
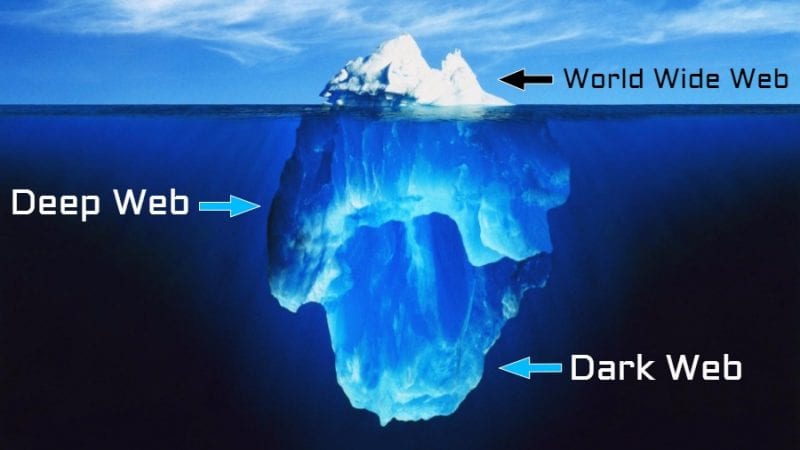
The concept of the internet as a network that can host many different types of network applications is important to grasp if you want to understand the difference between deep, dark, and surface webs. The “Deep Web” and “Dark Web” both sound intimidating, but that doesn’t mean they’re the same thing. While they’re related, knowing the difference can keep you safe from dangerous places on the internet and make you a hit at parties.
Consequently, using Tor (to visit the dark web) is something an average internet user does not do. And if you’re on that path, you better have reasonable explanations if it comes to that rare encounter with law enforcement. Most of that is legal, like your financial information in banks, social media accounts, email archives, cloud storage, academic journals, streaming libraries, etc. This structure benefits data protection, as financial records or research data stay confidential, but it complicates access for authorized parties.
Cybersecurity Issues
It allows you to search for images, maps, files, videos, social media posts, and more. The website is available on the surface web and has a .onion site. This means you can visit the site anonymously using the Onion browser, especially if you live under an oppressive regime. Since Hidden Wiki maintains all kinds of websites, ensure you don’t open something you don’t want to see. If you decide to venture into the dark depths of the deep web, make sure you’ve bolstered your device’s security with powerful privacy and security tools that can defend against dark web threats.
Is It Legal To Access The Dark Web?
This can benefit individuals seeking to protect their online activities from surveillance or tracking. Many of the email addresses and identities of your organization are exposed on the internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization. KnowBe4’s Email Exposure Check Pro (EEC) identifies the at-risk users in your organization by crawling business social media information and now thousands of breach databases. At the moment, the Dark Web is defined as a layer of information and pages that you can only get access to through so-called “overlay networks”, which run on top of the normal internet and obscure access. You need special software to access the Dark Web because a lot of it is encrypted, and most of the dark web pages are hosted anonymously.
How The Deep Web Is Different From Traditional Internet
That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy. The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you. It’s not a secret that ISPs (Internet Service Providers) and the FBI are tracking Tor users.
Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. Other sites explicitly block search engines from identifying them. The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing.

Similarities And Differences

Instead, sites have complex .onion addresses, making them difficult to find without the exact URL. It’s a part of the internet that’s less regulated and more shadowy, for better and for worse. You don’t need special tools or a special browser like you need to access the dark web (more about that later). Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information. Dark web sites are hidden by non-indexing, making them completely anonymous.
- This illegally-obtained data can allow malicious actors to gain access to confidential data, use stolen credit card numbers, and even bring down the entire remote infrastructure of an enterprise.
- In contrast, accessing the Dark Web comes with significantly higher risks due to its nature as an anonymous network.
- But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network.
- With many Tor-based sites being overtaken by police authorities across the globe, there is a clear danger of becoming government target for simply visiting a dark website.
- China uses what is known as the “Great Firewall” limit access to popular sites for this exact reason.
- In case you’re wondering how to access the deep web, chances are you already use it daily.
Unlike the dark web, which requires specialized browsers, deep web content often exists on the regular internet but remains inaccessible without proper authentication or direct links. The deep web refers to all internet content not indexed by standard search engines like Google or Bing. Perhaps the most notorious of the dark web sectors, it is indeed infamous for hosting illicit content, which contains marketplaces trading everything from drugs and weapons to stolen data. Also contained within it are forums for discussion that include everything from hacking services to human trafficking.
However, the main caveat is that the Tor network (an onion network that uses a series of nodes to provide you with access) is very slow. This makes it hard to use the Tor browser for surface web activities that require fast speeds (such as streaming, gaming, torrenting, making private calls, etc.). Not all mass thefts of data facilitated by the dark web have been motivated by money. The publicizing of Snowden’s actions led to a global spike of interest in Tor and a resulting rapid expansion of the network’s user base.
A top-of-the-line VPN network that ensures maximum security while accessing dark sites online. Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally.
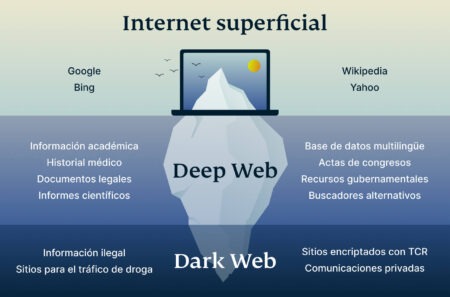
The dark web comprises purely non-indexed websites often used for illegal activity, whereas the deep web hosts paywalled and password-protected sites. In this dark web vs deep web guide, we discuss how they differ in terms of underlying technology, applications and more. If something cannot be found, even if it can be opened, then it too belongs to the deep web. If you configure Facebook to hide your profile from search engines, for example, then even if a search bot gets to it, it will have to ignore it.
Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use. Hidden Facebook is hardly the only social media client on the dark web. If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node. Though no one should bat an eye just because you’re attempting to access the dark web, keep in mind that in some countries, like the United States, even a simple foray can get you in trouble. By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP.
This essentially means that over 93% of Tor daily users use the dark web for legitimate reasons. The dark web and the deep web are often used interchangeably, but they’re two distinct concepts. The deep web is the part of the web that can’t be reached through typical search engines and often requires getting through additional layers of encryption to access. The dark web goes a step further, providing even more layers of encryption to grant users complete anonymity. However, the dark web’s anonymity makes it a breeding ground for criminal activities. People buy and sell illicit goods and services, share illegal files, sell criminal services, and carry out cybercrime, hate crimes, stalking, and more.