That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search. That’s why security teams need continued visibility into the dark web which enables them to mitigate the risk of data leaks, preventing further damage. Offering books for free, shadow libraries face the morality question of copyright vs. access to information and knowledge. Just Another Library is one such service, with a wealth of books covering computer programming, science, and niche hobbies (sailors’ knots, anyone?). It also offers works of art, course material, and audiobooks for download.
In due course, the framework was remodeled and made public as a secure browser. While it might appear tempting to venture into the dark web, it’s crucial to understand that the risks here are far more severe compared to the deep web. Therefore, if you do decide to explore it, exercise extreme caution. An easy way to find content on the dark web is to receive a link from someone who already knows about it. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy.
With its low 5% vendor fee, secure transactions, and verified sellers, it’s an ideal choice for buyers looking for a trusted marketplace. Markets that lack proper security often become targets for law enforcement, scammers, or cyberattacks. Radar Rundown Private search engines use the metasearch or proxy search model and the proprietary cr… STYX market features a robust verification process, making it look more exclusive. In fact, they have a Telegram channel to offer users with live updates. The platform supports Monero (XMR), Bitcoin (BTC), and several others to hide identities.
Fraudulent Markets

It offers outstanding privacy features and there is currently a discounted rate available through this link. Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware. Tails also protects you from possible malware, viruses, or keystroke loggers that may have already infected the computer, as it doesn’t run the operating system already installed on the device. Keep in mind what you’re looking for, find that information, and disconnect from the dark web.
Some alternative links are available, providing access to the marketplace. It’s recommended not to use new alternative links as they could just be planned exit scams. To prevent users from DDoS attacks, it provides personal marketplace domains to high-volume buyers and sellers. Moreover, this shop provides detailed statistics about each user profile on the platform, giving users a better idea of the vendors for the buyers and vice versa. This marketplace accepts payments via Monero but also supports the Escrow system.
Stolen Data And Identity Theft
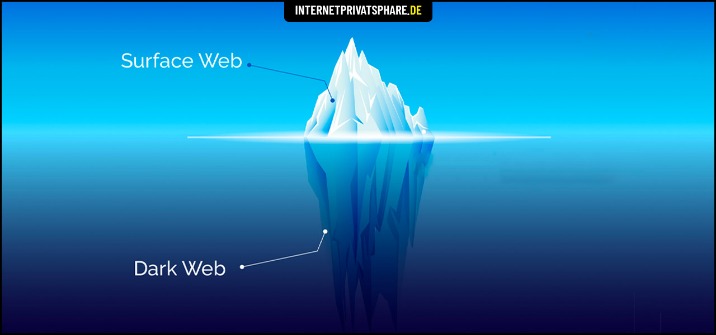
While not strictly a search engine, OnionLinks provides a directory-style resource that helps users discover various .onion sites across different categories. Torch is one of the oldest and most well-known dark web search engines, providing access to a vast index of .onion websites. Naturally, this makes the dark web a breeding ground for illegal activity. But onion sites can also serve nobler goals, like providing access to information and independent journalism in countries with government censorship. The dark web and the deep web are often used interchangeably, but they’re two distinct concepts.
- Radar Rundown Hiding your IP address is one of the best ways to protect your online activities from …
- As always, use Tor Links with care, as it includes onion links to dubious or illegal activity.
- Onion sites are dark web sites that can only be reached through online routing via Tor, in which encrypted data passes through multiple nodes before reaching its destination.
- The dark web allows people to access and share all sorts of illegal and explicit material without judgment or censorship.
- Apart from the best onion sites listed here, you must be careful with the Tor pages you visit.
What Services And Tools Are Available On The Dark Web?
Some believe STYX is the OG darknet market when it comes to financial crimes. It trades in hacked bank accounts, stolen credit card information, and other services that facilitate cryptocurrency laundering. Most darknet market administrators are now tightening access controls. Every potential participant’s credentials must be vigorously vetted before they can join. That way, they aim to create secure forums and limit outsiders like law enforcement. Likewise, law enforcement agencies each day continue to fine-tune their strategies to get past these networks.
Supreme Court will allow the FBI to search and seize any computer that’s using the Tor browser or VPN. Rule No.41 allows a federal judge to issue a search and seize warrant for any person who is using anonymity software like Tor. Now that you’ve completed the download, it’s time to install the Tor browser on your device. (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder. Then, simply click the operating system that you are using and download the file.
What Is The Deepest Search Engine?
Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything. The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. It works by sending internet traffic through volunteer-operated nodes all over the world. This network of over 6,000 relays hides your location, thus protecting you from online surveillance and third-party tracking by your websites.

Is It Illegal To Access The Darknet?
The remaining sites, including those on the dark web, won’t show up when you search Google—they can be accessed only with a direct URL, IP address, or deep web search application. The Hidden Wiki isn’t completely unrestricted, because it uses filters to block many of the scam sites found on the dark web. But like many dark web search engines, the Hidden Wiki provides info and links to certain sites that Google blocks. With over 1.5 billion indexed pages, Haystak may have more dark web sites than any other deep web search engine. The Haystak search engine does not track your data or compromise your privacy, although the free version will serve you occasional ads. Launched after the takedown of AlphaBay in 2021, Abacus Market has rapidly risen to prominence.
What You Can Buy On The Darknet Markets
A VPN enhances your privacy and security by encrypting your internet traffic and masking your IP address, making it difficult for anyone to track your online activities on the dark web. It’s essential to use a VPN, like Forest VPN, to secure your data, avoid clicking on unfamiliar links, and never disclose personal information. Additionally, using antivirus software and strong passwords can further protect you from potential threats. For example, concurrent with the takedown of Hydra was the sanctioning of Garantex, the Moscow-based exchange that made multiple transactions with Hydra-linked addresses.
It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web. Background research tasks included learning from past drug lords, researching legal matters, studying law enforcement agency tactics and obtaining legal representation.

It has gained a reputation for being a reliable source of high-quality data for cybercriminals. Its focus on financial fraud and high-value transactions has attracted a dedicated user base, contributing to its growing reputation and market value. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected.
Silk Road And Early Markets
Yes, a VPN adds an extra layer of privacy and security when accessing the dark web, reducing the risk of tracking and surveillance. OSINT professionals must venture where conventional tools can’t reach—and the dark web is one such frontier. Avoid downloading files, clicking on unfamiliar links, and sharing personal information. Additionally, do not attempt to buy anything on the dark web as most transactions are illegal and can lead to scams. Typically, you can find dark web URLs through forums, databases, or by talking to others who frequent those sites.

While many dark marketplaces have been shut down by authorities, new ones soon appear in their place. Using a dark web search engine is a great step towards enjoying a more secure experience while shopping on the platform. Not all marketplaces you want to visit can be accessed through regular search engines. In addition, mainstream search engines also track your searches and collect personal information.