In fact, your data might be up for sale on the dark web already. Therefore, you need to take your privacy seriously and start by using strong and unique passwords for every online account you open. The dark web is not a place that you can venture into without protection and caution; a slight slip-up can lead to major consequences. Perhaps, the lack of rules and anonymity of the dark web can be tempting, but those are the same things that make it a risky environment. Moreover, it’s not only the entertainment industry that gets hit; some sell cracked versions of the most expensive software, and others offer pirated eBooks and academic material at cheap prices. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacyRadar.com page.
Stolen Data And Identity Theft

“Satisfied customer, will be back,” writes one user on the product page of a meth dealer with the handle shardyshardface. “Excellent,” reads a plaudit posted by a buyer of the opiate oxycodone. “Bravo,” says another for a $5 sample of fentanyl, one of 18 reviews posted on the product’s profile page in the last week. In all, Empire lists over 18,000 narcotic offerings, including hundreds for oxycodone alone.
Overcoming The Challenges Of Policing Drug Trafficking On The Dark Web
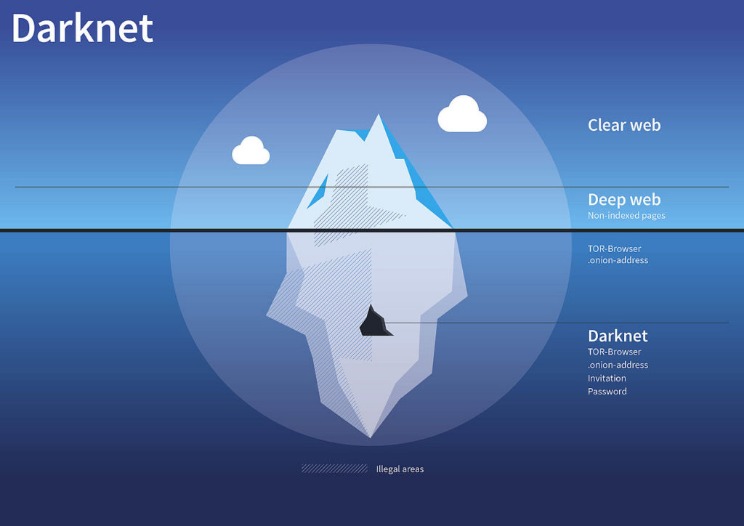
KEY TAKEAWAYS The Deep and the Dark web are the hidden part of the internet. When you use it, all the web traffic automatically routes through Tor. If the operating system detects any non-anonymous connection, it blocks it, thus ensuring maximum online protection. The readers like you support Beencrypted to help keep up the good work.
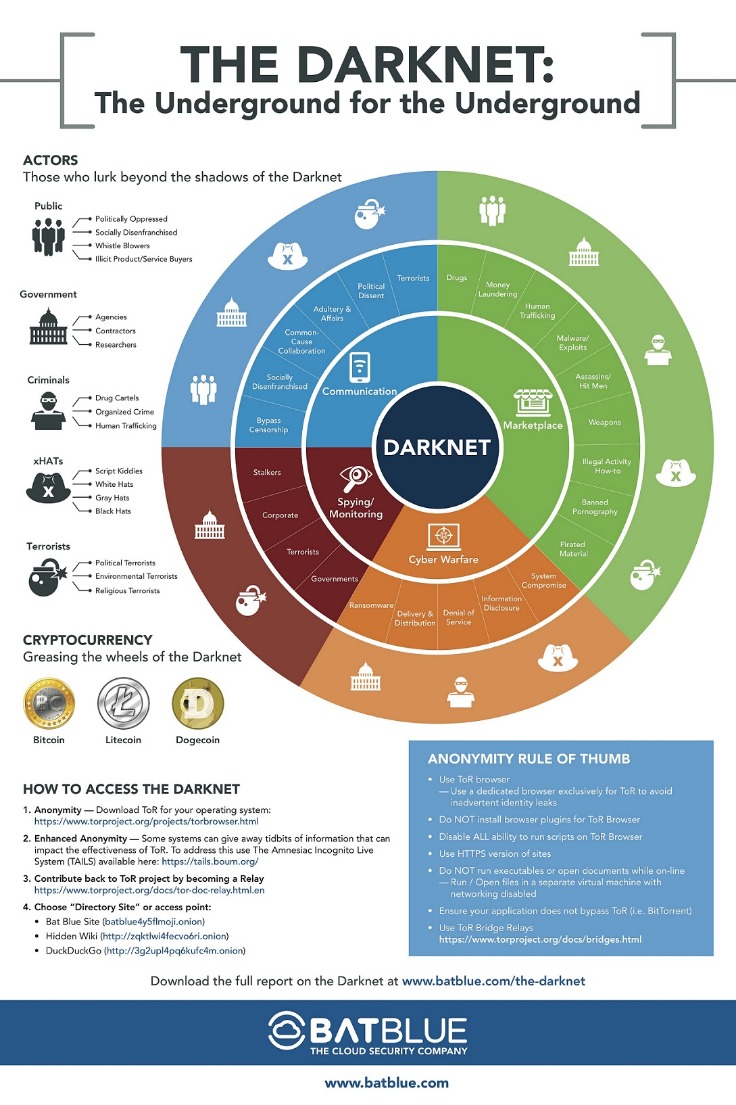
Ethically, they must minimize harm, responsibly handle any stolen or sensitive data (often notifying victims or law enforcement), avoid entrapment, and maintain research integrity. An award-winning cybercrime threat intelligence firm, KELA’s mission is to provide 100% real, actionable intelligence on threats emerging from the cybercrime underground, to support the prevention of digital crimes. See how our intelligent, autonomous cybersecurity platform harnesses the power of data and AI to protect your organization now and into the future. Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks. Darknets also serve as a platform for whistleblowers and privacy advocates.
If he leaves it there for a while, a drug-sniffing dog will smell the cannabis through the metal of the gas tank, the gas, the concrete, the PVC pipe, and the plastic bag because it permeates. Nothing in this world is solid, everything is made up of atoms and even atoms are mostly empty space. Permeation can go through anything, but it may take longer for some substances. XMR hides transaction details, unlike BTC, which dropped 40% in use due to tracking risks since 2023. The top performers of 2025, ranked by trade volume and market influence.

Features That Make WTN Market A Secure Platform
The information here may be outdated and links may no longer function. Please contact if you have any questions about the archive site. I walked into the local PO that day with the factory reset button open on my phone. I had always envisioned that in the event of a CD that I would have time to erase my phone. My stupid phone was the very first thing that was grabbed by LE.
Beacon Cybersecurity Newsletter
Some vendors develop outstanding techniques, which make drug detection almost impossible. Such dealers are worth their weight in gold, and you’d better save their contact details not to lose touch in case a dark web market shuts down. Navigate darknet markets wisely with these essential and updated do’s and don’ts. Stay safe, avoid pitfalls, and make informed decisions for a secure online experience.
- Every investment and trading move involves risk; this is especially true for cryptocurrencies given their volatility.
- It advised people to be cautious as there was a dangerous batch of drugs, specifically fentanyl, circulating.
- All products featured on WIRED are independently selected by our editors.
- With Tor installed, you’ll next need to find a darknet marketplace domain to visit.
- On Dread, the reactions to the recent law enforcement activity were a mix of dismay and defiance.
- Some things, like medical records, driver’s licenses, and passport information.
Cryptocurrency Wallets For Safe Transactions
One of the most common is the exit scam, where a marketplace suddenly disappears and takes everyone’s money with it. It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. The darknet’s a money machine, raking in billions through crypto.
- By eliminating unnecessary intermediaries, they can reduce costs and ensure a reliable supply of illicit goods.
- Law enforcement agencies monitor it for criminal activities, but legitimate users rely on it for privacy protection.
- Investigators discovered a plethora of black market goods available on Silk Road.
- We read every piece of feedback, and take your input very seriously.
- You can find drugs, weapons, stolen data, and counterfeit documents on these marketplaces.
- Vendors utilize secure communication channels, employ stealth techniques, and establish a solid customer base.
Account Hacking Scam
JCODE also targets the trafficking of weapons and other illicit goods and services on the internet. If you cannot think of any valid reasons why the stuff costs so cheap in a darknet marketplace, it’s likely a low-grade product. Use logic and math to find goods in the popular vendor shops perfectly balanced in terms of price and quality.
Using a dark web search engine is a great step towards enjoying a more secure experience while shopping on the platform. Not all marketplaces you want to visit can be accessed through regular search engines. In addition, mainstream search engines also track your searches and collect personal information. Cybercriminals on the dark web marketplace always look for new victims to target them with scams or infect their devices with malware, spyware, or adware. Thus, use the best antivirus software that protects against these online threats.
They can always set up a sting and a friendly neighborhood gangster to sell drugs online. Make sure all listings have up-to-date reviews and that buyers are actually buying, and that the market is actually working. If there are a lot of listings with no current reviews, it could mean that people have already left the market, or there could be something else going on. Markets that lack proper security often become targets for law enforcement, scammers, or cyberattacks.
Investigators discovered a plethora of black market goods available on Silk Road. There were various illegal drugs including heroin, Ecstasy, LSD, marijuana and steroids. Also, illegal weapons, books on how to construct bombs, counterfeit identification and counterfeit merchandise. While there are many sites that facilitate illegal activities, there are also legitimate sites that provide valuable resources, including educational materials and tools for privacy protection. While it’s true that it hosts illegal activities, it’s also a haven for those seeking privacy from prying eyes.
Always ensure you’re using the correct link to avoid phishing attacks. If the primary link is down, many markets offer verified mirror links that provide secure, uninterrupted access. A repository preserving darknet market data, including vendor lists, PGP keys, listings, and more for research & intelligence purposes. Cyber investigations sometimes begin as traditional in nature then progress into the cyber environment. HSI was one of the primary agencies on the Silk Road investigation that revealed large-scale illegal drug and contraband smuggling through the U.S.
Selling Illicit Goods On Dark Web Marketplaces
If you are planning to make a purchase on the dark web, you should really take the time to learn how PGP encryption works. It’s actually not that difficult and this guide aims to make it as easy as possible for beginners. PGP stands for ‘Pretty Good Privacy’ and is an encrypted method of sending and receiving messages which can only be read by a specifically intended recipient. Many markets provide an auto-encryption option when providing a vendor with your address, but in this instance you are putting your trust entirely in the market. For best security, you should encrypt yourself to be 100% sure that your message cannot be read by anyone else.
Related Posts
Firstly, national orders will hit your post box faster than international. Secondly, packages sent locally get intercepted less frequently. Post office staff have no right to open parcels, but when workers find something suspicious, they call the police. Therefore, as long as a packet doesn’t smell like cannabis and powder or liquid doesn’t leak from the carton, it won’t be flagged.
Despite being legal in most countries, CBD oil can be hard to obtain in certain regions. The darknet can take care of this (and much more) by discretely delivering the legal compound to your door with no questions asked. White was among several individuals in Britain who were convicted as part of the operation against Silk Road. He was arrested in November 2014, when Chowles led the NCA’s work analyzing devices seized from White and extracting both data and cryptocurrency from those devices.