It’s also a good idea to set up a VPN for an extra layer of protection. You can access onion sites only through the Tor browser or special network configurations. On the Tor network, the onion domain name reflects the fact that, like the layers of an onion, the Tor browser consists of layers of protection. Tor encrypts traffic, masks your IP address, blocks trackers and browser fingerprinting, and doesn’t store a record of your activity. Tor Metrics is a set of tools and data provided by the Tor Project that offers insights into the performance, usage, and activity of the Tor ecosystem and its nodes.
- The combination of Tor markets and cryptomarkets has created a robust ecosystem where users can trade drugs with confidence, knowing their identities and activities are protected.
- This operation exemplifies how international collaboration, intelligence sharing, and advanced cyber-forensic techniques are essential in combating these hidden marketplaces.
- The integration of Bitcoin as the primary currency has further streamlined operations, offering users a decentralized and untraceable payment method.
- Incognito Market shares the same #1/#2 market status based on the number of vendors.
- Fraud-related products, consumer electronicselectronics, self-defense products, and even hosting.
Which Darknet Market Are Still Up
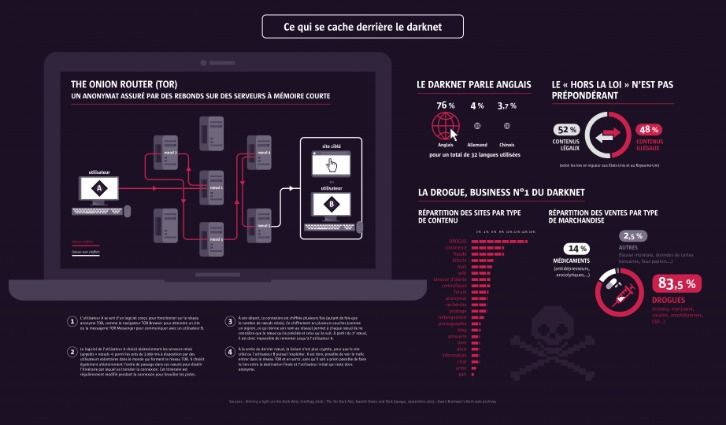
The evolution of cryptomarkets has led to improved interfaces, enhanced security protocols, and a wider range of products, making them the preferred choice for many. These platforms leverage advanced encryption technologies, such as Tor and onion routing, ensuring that user identities and transactions remain anonymous. The darknet has become a cornerstone for secure and reliable drug trade, offering users a platform that prioritizes privacy and efficiency. In 2025, the best darknet markets have refined their systems to ensure seamless transactions and user safety.
Multi-vendor Darknet Drug Markets

The EDTF is the premier money laundering task force in the nation and comprises more than 200 law enforcement personnel representing approximately 35 federal, state and local law enforcement and regulatory agencies. The EDTF encompasses a standalone Cyber Division as part of an effort to stay abreast of emerging criminal threats and in keeping with current and future investigative priorities. The EDTF’s mission is to disrupt, dismantle or render ineffective organizations involved in the laundering of proceeds of narcotics trafficking and other financial crimes. Since its inception in 1992, the task force has been responsible for the seizure of approximately $600 million and more than 2100 arrests. Clicking on random onion links is quite risky and isn’t recommended.
Does The CIA Have An Onion Site?
Viruses, ransomware, and other types of malware are more common on onion sites than on the normal internet. Many pages have poor encryption standards and no other protections, so simply visiting a Tor site can infect your device. Insights like these help researchers and advocates understand how and why Tor is being used. With this info, the wider online community can grasp Tor’s impact and its ability to provide secure and anonymous internet access. Wherever you go online, but especially if you’re on dark web websites, using a VPN helps you secure your communication data and protect personal information you send or receive. Avast SecureLine VPN encrypts all of your internet traffic to help block hackers and keep snoops out.
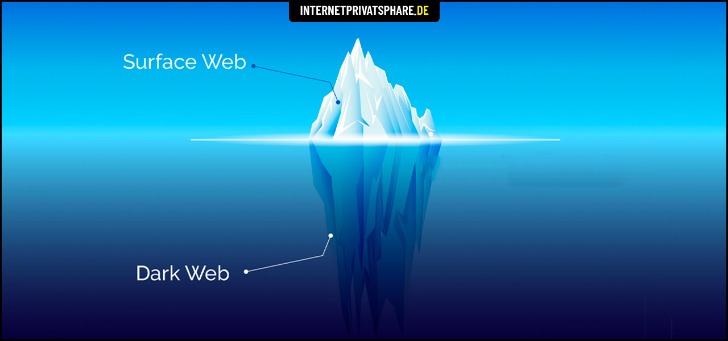
The marketplace is well-known for its bug bounty programs and robust security mechanisms, including mandatory 2FA. The takedown of Archetyp Market is a clear signal that law enforcement agencies, supported by advanced blockchain intelligence, can disrupt even the most entrenched illicit platforms. But the resilience and evolution of these networks underscore the need for continued cross-border collaboration, technical innovation, and real-time monitoring to stay ahead of the next generation of darknet threats. In the image above, (a) is the surface web, which includes publicly visible websites like blogs, shopping sites, and news sites. (b) is the deep web, which consists of sites that require a login to access like email accounts, banking portals, and subscription services.
Trusted Directories And Forums (stay Away From Hidden Wiki)
Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.

Hundreds Nabbed In Global Crackdown On Dark-web Drug Marketplace
Ruheni Mathenge specializes in writing long-form content dedicated to helping individuals and businesses navigate and understand the constantly evolving online security and web freedom worlds. His articles have appeared in many respected technology publications. Surfshark supports unlimited simultaneous connections to protect as many devices as possible.
Agentic AI-Powered, Intelligence-Driven Unified Cybersecurity Platform
That said, you still might get malicious links in your search results, so you still need to proceed with caution with any page DuckDuckGo takes you to. So take this guide as you explore where to go on the Tor Browser without risking your online security. This website is made public with the intention to aid the Internet users with navigation of the so called dark web. We have never received a compensation in any form for operating this website. We are not responsible for any harm or loss you may receive by following links listed on this site. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online.

Deploying 300 officers across multiple countries simultaneously is a logistical feat, reflecting a high level of international cooperation. This cooperative model could serve as a blueprint for future operations targeting other illicit darknet platforms. Archetyp’s use of Monero cryptocurrency highlights the challenges authorities face in tracking financial flows on the darknet. Monero’s privacy features make tracing transactions notoriously difficult, adding complexity to investigations.

The website operated in a format similar to other e-commerce platforms, with product listings, ratings, and user profiles. Vendors offered a range of drugs, including cannabis, cocaine, MDMA, LSD, benzodiazepines, and methamphetamine.17 Substances could be searched for by category, place of origin, and destination. These included an advanced encryption program known as “Pretty Good Privacy” and a cryptocurrency called Monero. Unlike Bitcoin, which records every payment on a public ledger, Monero conceals all transaction details by default, which makes them nearly impossible to trace. Forums and magazines play a crucial role in keeping users informed about new market links and updates. Platforms like Dread and Darknet Live provide real-time discussions, vendor reviews, and security tips, ensuring users can navigate the darknet safely and efficiently.
We do not engage with darknet markets; our mission is exclusively dedicated to providing information for research and educational purposes. For those prioritizing variety, EclipseMarket stands out with its extensive catalog of pharmaceuticals, recreational drugs, and rare substances. The platform’s user feedback system allows buyers to make informed decisions, while its integrated dispute resolution mechanism ensures fair outcomes in case of disagreements. mark it means it has been verified as a scam service and it should be avoided.|Users benefit from the convenience of browsing extensive product catalogs, secure communication channels, and reliable delivery systems. As these platforms continue to evolve, they are expected to further refine their features, ensuring that they remain the preferred choice for secure and private transactions in the digital age. One of the key features of top-tier darknet markets is their use of Tor networks, which provide users with a high level of anonymity. By routing traffic through multiple nodes, Tor ensures that IP addresses are concealed, reducing the risk of exposure.|”Excellent,” reads a plaudit posted by a buyer of the opiate oxycodone. “Bravo,” says another for a $5 sample of fentanyl, one of 18 reviews posted on the product’s profile page in the last week. In all, Empire lists over 18,000 narcotic offerings, including hundreds for oxycodone alone.}
Cypher Marketplace
A single study can’t definitively prove whether the dark web offers a safer supply. But these results suggest that, while some substances were indeed less likely to be adulterated, purchasing there is not a silver-bullet harm reduction strategy—and that testing remains vital whatever the source. By paying close attention to where adulterated substances were purchased, local drug checking services can help participants make more informed decisions to protect their health. In Barratt’s eyes, these far-from-straightforward results underscore the importance of expanding drug checking services. When you can’t necessarily count on cryptomarkets offering a safer supply, local drug checking becomes even more essential.



