This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session. The Tor browser allows you to browse the internet anonymously and visit inaccessible sites. It will encrypt your traffic and data so no one can intercept it. Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there.
Related Articles From The Safe Browsing Section
Facebook is aware of attempts by many governments to restrict access to a tool that allows strangers across the web to talk and collaborate freely. While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored. The internet’s favorite alternative to Google made a name for itself by not logging your search activity yet still providing decent results. This focus on privacy makes it the Tor Browser’s default search engine and one of the best onion search engines. Torch is one of the oldest and most popular onion search engines on the dark web, serving over 80,000 requests per day. Torch is funded primarily through advertising—purchased in BTC, of course—which is why you’ll find the front page blanketed with old-school banner ads of dubious origins.
Avoid Suspicious Links
Moreover, due to its popularity, many copycats of the Hidden Wiki exist. So don’t be surprised if you encounter different versions that claim to be genuine, and be very careful. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page.

Darknet Markets
It provides an .onion URL and an interface for you to manage your Tor site easily. It also boasts that no personal information is required to use the service, and payment can be made with cryptocurrency. Keybase also offers extremely user-friendly secure chat and file-sharing services through its app. Based in Switzerland, ProtonMail is an encrypted email service that is very popular with cryptocurrency enthusiasts. Feather is a free and open source Monero wallet available on most major computer platforms. Monero is a crypto currency that can be used to conduct transactions anonymously on a peer to peer level without any centralized authority watching over..
Besides, it has a huge and highly active user community that discusses credential lists, hacking tools, email and password combos, vulnerable software, and several other things. It’s so well managed that the platform is multilingual as it features up to 12 language-specific sections, with the French sub-forum being the most active. Also, it provides users with an escrow service, which adds an extra layer of trust when they conduct transactions on this notorious platform. Nulled is an enduring forum that specializes in nulled leaks, cracked software, and premium account access.
Torzon Market

Experienced blogger with a strong focus on technology, currently advancing towards a career in IT Security Analysis. I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world.
Google Feud
Onion sites are far safer to use as they are hidden deep within the deep web. Also, since users can only access them using the Tor browser (with its high-end encryption), users can be rest assured their identities and locations remain hidden. Like regular browsers with domain names, the Tor browser also has its own domain designation. These “onion” sites are only accessible on the dark web and bear the “.onion” domain at the end of the URL. This is no different from the “.net” or “.com” of the regular Internet.
- You’ll be surprised to know that you can access Facebook via the dark web by using the official Facebook .onion site.
- The sub-reddit isn’t very active but if the Deep web interests you, this Subreddit should too.
- ProPublica’s work is all legal, so the .onion website isn’t much different from what you would find online.
- Speak your mind here without fear, as onion links are immune to censorship.
- Therefore, use NordVPN to view search results and browse anonymously.
- Opening the onion links is very easy from the Tor browser, which you need to download and install in advance.
How To Delete Yahoo Account In 2025
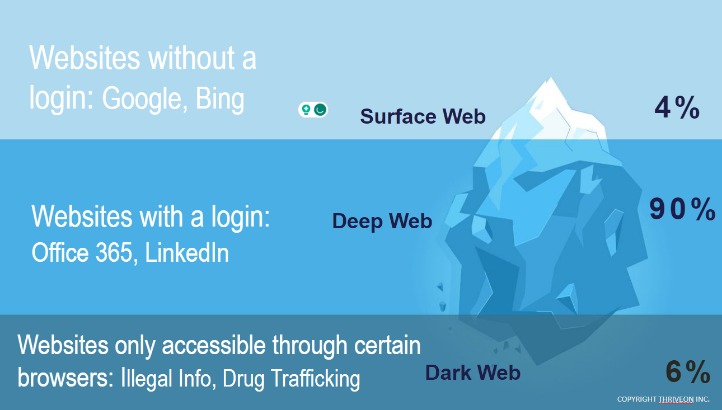
Also referred to as “non-indexed” content, it’s any content hidden behind some kind of access control such as a log-in or code word. It contains 7,500 terabytes of information, compared with only 19 terabytes of information in the “surface” web. To look at it in a different way, it makes up between 90% and 95% of the internet. The dark web and the deep web are often used interchangeably, but they’re two distinct concepts. No, onion links can only be accessed through Tor browsers, which provide the necessary encryption and anonymity to browse the dark web securely.
They know how to process the information and get it to the correct law enforcement agencies internationally. While Tor offers anonymity on the dark web, your online activities leave breadcrumbs that can reveal your identity. That is why you should only use a reliable VPN like ExpressVPN or NordVPN for additional security and privacy. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user. In some countries, evading government restrictions to seek new political ideologies is punishable. For example, China uses the Great Firewall to block access to Western sites.
- We also made sure to select only sites that have been around for a considerable amount of time without being taken down or being the subject of any privacy or security scandals.
- Keep in mind that you’ve to use very specific keywords when searching.
- The email service is available both on the surface and on the dark web.
- Many people see hacked information and stolen card data being sold on the dark web.
- Even without the code, you can visit the security section to get tips on improving your daily life privacy.
- The “Dark Web” is a sub-section of the deep web and is largely responsible for the deep web’s bad reputation.
How To Get On The Dark Web? Is It Illegal To Browse?
The best thing is to actually understand how to find the fresh, new links. You only need to upload your PGP key or let the platform create one. Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile. Established in 2012, the platform is a time capsule that collects snapshots of websites. These onion addresses will remain online even if the original page disappears.
BBC News /portuguese Brasil

The Bitcoin core website posts the latest updates to the open-source Bitcoin software, which is programmed to decide which blockchains contain valid transactions. The users of Bitcoin Core only accept transactions for that blockchain. Making it the bitcoin blockchain that everyone else wants to use. Previously, the Silk Road was the most popular darknet market, created by Ross Ulbricht, AKA Dread Pirate Roberts. So, to find a current list of the most popular markets (such as White House Market or Empire), you can go to either Darknetlive or Dark.Fail. Dread is a great alternative if you fancy checking out another dark-web-based social network or forum with news and discussions.
Marketing
Cracked is arguably the most accessible forum when compared to other dark web counterparts. Exploit.In is one of the most visited (and notorious) dark web platforms from long ago, which operates in a Russian-speaking landscape. It’s a major threat to monitor as it operates on both the Tor and the surface web, which makes it accessible from several fronts. Despite all the attacks, blocks, and the constant pressure from the authorities, the forum remains active. The fact that it discusses vulnerabilities, legal tools, data leaks, and malware attracts prominent threat actors constantly.
Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously. The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN.



