Tor has an in-build slider which lets you adjust the level of security. This means that the JavaScript will be disabled by default on every website and some symbols and images will not be displayed. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. For instance, if you want to buy a laptop or a smartphone, you can try your luck in one of these shops. Sure, you can use other cryptocurrencies if Bitcoin’s not your cup of tea.
International collaboration is essential in enforcing laws against dark web crimes due to the global nature of these networks. Legal frameworks like the Budapest Convention on Cybercrime facilitate cooperation among countries, providing mechanisms for sharing information and evidence. However, jurisdictional differences remain a significant hurdle, as varying laws and definitions of cybercrime complicate extradition processes and prosecutions. If you discover your data on the dark web, act quickly to minimize the damage and report the incident to relevant authorities to ensure any necessary legal action is taken. Despite its legitimate uses, cryptocurrency’s untraceable payment nature has raised concerns around money laundering and illicit trade, driving regulatory scrutiny.
- Instead of search engines, you’ll need to rely on directories or specific .onion links.
- This makes it almost impossible to track your dark web activity from beginning to end.
- To be on the safe side, we recommend combining the Tor or onion browser with a secure VPN, such as NordVPN.
- Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal.
- The Tor browser allows you to browse the internet anonymously and visit inaccessible sites.
- Cybersecurity professionals play a crucial role in monitoring and mitigating the threats that originate from the dark net.
The Dark Web offers an avenue for these individuals to exercise their freedom of expression, access information, and communicate securely without being subjected to surveillance or persecution. Anonymity can empower individuals to actively participate in political activism, share knowledge, and express opinions without fear of retribution. The Dark Web, despite its association with criminal activities, serves as a platform for individuals seeking privacy and protection. Journalists, activists, and human rights advocates often utilize the Dark Web to share sensitive information, whistleblow, or communicate securely with sources in repressive regimes. The Dark Web can serve as an essential tool for promoting free speech and anonymized dialogue in regions with restricted internet access or in the face of governmental censorship. Lastly, the Dark Web is a small portion of the Deep Web that’s purposefully obscured and can only be accessed through specific tools.
Friends & Links
Be aware of scams and frauds and thoroughly research any darknet markets or vendors before making any transactions. When accessing the Dark Web, it’s crucial to protect your personal information. Avoid using your real name, email address, or any personally identifiable information. Create anonymous usernames and use secure passwords for any accounts you create. The Dark Web operates on a network known as Tor, short for The Onion Router. Tor was originally developed by the United States Naval Research Laboratory to protect communication privacy.
Alternatives To Tor
Before visiting any dark websites, get comprehensive cybersecurity software to help protect yourself from threats you may encounter. Dark web browsing is not as simple as regular web surfing, but there are some tools you can use to chart your journey. Dark web search engines and forums like Reddit can help you find reliable dark websites, and you’ll need to use a dark web browser to visit them. The Tor network combined with a VPN is one of the safest ways to get on the dark web. Many internet service providers (ISPs) and governments are suspicious of Tor use, but a VPN will hide your internet activity and help prevent anyone from knowing that you’re using Tor.

For recommendations on choosing a VPN, look for expert reviews and articles. If you’ve ever checked your medical results online through a portal that required a login, you were navigating the deep web. It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. However, most are outdated and have not kept up with the changing landscape.
Detailed Steps To Access The Dark Web Using Tor
The Deep Web forms a more expansive but hidden layer beyond the reach of conventional search engines. This section comprises content requiring specific permissions, login credentials, or specialized tools for access. Examples include password-protected websites, private databases, and subscription-based resources, contributing to a broader yet less visible realm on the internet. The Open Web, also known as the surface web, constitutes the most accessible layer of the internet, readily navigated through popular search engines like Firefox, Google, Bing, and Yahoo. It encompasses public domains such as websites, social media platforms, news sites, and online stores—content accessible to anyone with the help of the internet and a web browser. In the deep net, web crawlers are blocked from accessing web pages to gather information for indexing, so the content remains hidden.
The Dark Web: Risks And The Role Of Standards
If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough. If you’re trying to hide from an oppressive government or want to be a whistle-blower for something illegal, take as many steps as you can to be safe. Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection. Plus, it features a built-in VPN to encrypt your connection, hiding your IP address and online activity, for more anonymous and private browsing. However, finding information can be challenging as the dark web doesn’t use a centralized index to locate content. Instead, users rely on dark web search engines like DuckDuckGo or directories, such as the Hidden Wiki and its offshoots, to find .onion websites.

Best VPNs To Access The Dark Web Safely
Therefore, you should stay cautious and avoid clicking when accessing the dark web. Doing so will protect you from accidentally accessing illicit content or becoming a victim of malware. While Tor offers anonymity by routing your traffic through a decentralized network of nodes (onion routing), it shouldn’t be your only line of defense for privacy. Malicious actors and government agencies can run Tor nodes, compromising privacy and security. In fact, there have been instances where attackers controlled hundreds of Tor nodes.
A Dark Web Search Engine
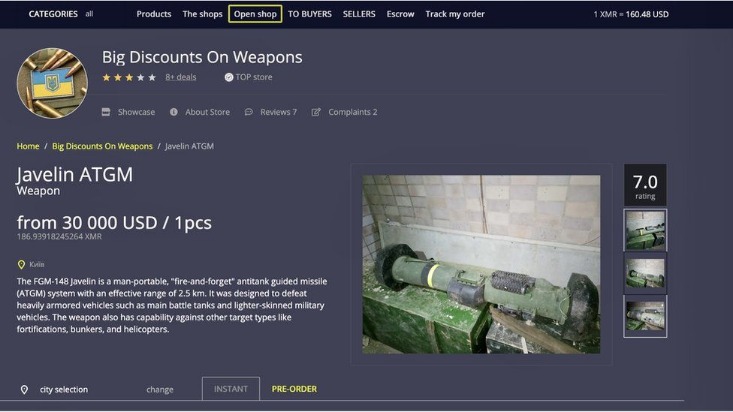
As much as the Darknet contains even the “good” stuff, it’s not a place you need to stumble about blindly without proper dark web safety. Cybercriminal groups like DDOS have carried out over 140 cyberattacks on companies since Bitcoin’s emergence in 2014. The attacks have led to the formation of other cybercriminal groups and Cyber Extortion. According to recent research, Bitcoin tumblers are increasingly used for money laundering. The urban legend of ‘Red Rooms’ that features live murders has been debunked as a hoax. Some websites monitor and analyze the dark web for threat intelligence.
Can I Use Tor To Browse The Surface Web?
Using a VPN with Tor (commonly referred to as “Tor over VPN” or Onion over VPN”) adds an essential layer of protection. It hides the use of Tor from your ISP and protects you if your Tor connection is compromised in some way. Downloaded files could have malware in them that may be designed to de-anonymize you or infect your device. If you must download something from the dark web, only download files and run them using a completely isolated virtual machine.
Although the official Tor Project advises against VPN over Tor, both methods are superior to not using a VPN at all. Put simply, the deep web is all the information stored online that isn’t indexed by search engines. You don’t need special tools or a dark net browser to access most of the deep web; you just need to know where to look. Specialized search engines, directories, and wikis can help users locate the data they’re looking for.
Are Dark Websites Illegal To Use And Visit?
If you go looking for trouble on the dark web, chances are you’ll find it. If you stick to using it for legitimate and legal purposes and proceed with caution, you can have a perfectly safe and secure experience. They contain text and images, clickable content, site navigation buttons, and so on. Infamous criminal sites live there, but so do popular, well-known sites and brands. Perhaps you’ve heard the infamous stories about Silk Road, the online marketplace used to sell illegal drugs with bitcoin behind the veil of the Tor browser. Launched in 2011, it is known to be one of the first online platforms of the dark web.