You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web. The social media giant is also aware of the many attempts by repressive regimes to restrict its access.
Secure Your System And Mental Well-being

No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet. Again, not all the dark web is used for illicit purposes despite its ominous-sounding name. It offers outstanding privacy features and there is currently a discounted rate available through this link.
However, it soon became a double-edged sword as malicious actors began to exploit its capabilities for illicit purposes. Dark markets, on the other hand, are platforms within darknets where illicit transactions occur. These marketplaces facilitate the exchange of everything from stolen credentials and drugs to weapons and hacking tools. The anonymity and encryption provided in dark markets create a haven for cybercriminals and nation-state actors to buy and sell dangerous assets while evading detection. Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites.
Researchers Daniel Moore and Thomas Rid of King’s College in London classified the contents of 2,723 live dark web sites over a five-week period in 2015 and found that 57% host illicit material. Personal and financial data are commonly sold on dark markets, facilitating identity theft and fraudulent activities. The significance here lies in the potential damage to individuals and businesses. Companies must implement strong data security measures, employ encryption, and monitor for data breaches to protect customer and employee information. NordVPN offers a 30-day, no-risk trial subscription when you sign up on this page. This provides a full month’s access to all of the features of the #1 VPN for the Dark Web.
Was Sind Onion-Seiten?
Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web. The dark web isn’t just one sketchy marketplace hiding in a corner of the internet; it’s more like a messy, unregulated community with everything from freedom fighters to full-blown cybercriminals.

Types Of Dark Web Sites (and What Really Goes On There)
Its goal is to offer anonymous access to the content without being censored, no matter where you live. The good news is that the BBC Onion site is an international edition. As a result, it not only focuses on the UK but also provides worldwide news. If you choose to visit the dark web, you must take the necessary measures to protect your privacy and security. Check out these best onion sites to access the dark web securely and anonymously.
Orbot: Tor Für Android
The platform is protected from government interference and malicious attacks to protect the user. In addition, it ensures that no record of communication is stored. Unlike other search engines, it does not collect or share web activities and personal data of users. The dark web, which is what I’m discussing here, is a small subset of the deep web, and refers to websites that are specifically trying to stay out of sight.
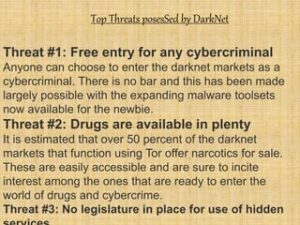
What Are The Risks Of Using Dark Markets?
That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy. The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you. It’s not a secret that ISPs (Internet Service Providers) and the FBI are tracking Tor users. Obviously not all Tor users, but you never know whether someone might be looking into you. It’s important to arm yourself with a good VPN (Virtual Private Network) when you want to enter the dark web to protect your privacy and anonymity.
- However, engaging in illegal activities on the darknet is against the law and can result in serious criminal charges.
- Besides, victims of crime may want to hide their identities from their perpetrators.
- There are several whistleblower sites, including a dark web version of Wikileaks.
- The advantages of I2P are based on a much faster and more reliable network.
- Obviously not all Tor users, but you never know whether someone might be looking into you.
Purchases through links on our pages may yield affiliate revenue for us. We review and list tools and products without bias, regardless of potential commissions. With Tor Browser, you are free to access sites your home network may have blocked. Your traffic is relayed and encrypted three times as it passes over the Tor network.
The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones. For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”. For example, you can only find your Facebook friends, photos, and other information by logging into your Facebook account and finding the information there. On the deep web, you can find such “private” information on web pages. So, even though it does exist on the internet, Google doesn’t index any of these pages or content. The US government created the dark web to help its spies communicate and exchange information securely.
Was Ist WPA2 (Wi-Fi Protected Access ?
The dark web is a part of the internet that you only step into with a specific tool (Tor, more on this later in the article). Though people usually think of dark websites as the wrong online place, that’s not the complete truth. Although the underground internet world is rife with everything bad, it also hosts positive elements. With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with.
- Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there.
- In this system, cryptocurrency is held by a trusted third party until the buyer receives the product or service as described.
- The dark web has flourished thanks to bitcoin, the crypto-currency that enables two parties to conduct a trusted transaction without knowing each other’s identity.
- Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion.
The surface web (often referred to as the “visible web”) is the portion of the web available to the general public and indexed in the standard web search engines such as Google, Bing, and Yahoo. Dark web forums are online platforms that can only be accessed using anonymous networks, mainly Tor…. While browsing online, you might have noticed that the websites you are visiting have URLs starting … It hosted over 7,000 .onion categorized links to make surfing the web easier. One of Daniel’s impressive features was the built-in functionality that showed whether a particular dark website is online. After more than a year of no updates, the site admin shut it down, reasoning that he couldn’t keep the list of onion links up-to-date.

What To Do If You See Something Illegal

Deep web content includes anything behind a paywall or requires sign-in credentials. It also includes any content that its owners have blocked web crawlers from indexing. Dark markets continually adapt and evolve to stay ahead of law enforcement and security measures. As one marketplace is taken down, another often rises in its place.
Many services that are allegedly offered on the dark web are scams. Some services are genuine; you can get what you want at an agreed fee. However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address.
Kann Man Mit Einem VPN Auf Das Darknet Zugreifen?
This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity. Hence, you never know when a popular .onion site is going to vanish, or even die. Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though).