You can also check out this ultimate dark web safety guide to browse safely. Anonymity of the dark web is one of the main draws for using onion sites, and most dark web links use a “.onion” domain. This is usually due to the sensitive nature of the businesses or services they offer. Onion sites may offer secure access to cryptocurrency wallets or anonymous email clients.

This search field allows you to perform regular, but now anonymized, web searches through DuckDuckGo’s Tor site. Stay informed about the latest darknet marketplaces, secure browsing practices, and privacy tools. Share them in the comments below or explore more articles in our Dark Web Insights section.
Enjoy More Secure Browsing With A VPN
That’s why security teams need continued visibility into the dark web which enables them to mitigate the risk of data leaks, preventing further damage. This process makes tracing the user’s location and activity nearly impossible. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024.
- To access .onion websites securely, you’ll need the Tor Browser, a privacy-focused tool designed specifically for anonymous browsing.
- This .onion link makes it impossible for hackers to impersonate your profile.
- By following simple yet crucial safety measures, you can effectively minimize risks and safely satisfy your curiosity about the hidden parts of the internet.
- These top 10 dark web search engines are important for research, evidence collection, finding hidden resources, intelligence, and various other resources that are not easily accessible.
- This network, known as the Tor network, is a series of volunteer-run routers, or relays, that can talk to each other (as well as normal devices on the internet).
There are many legitimate uses for dark web services and communication. As search engine crawlers do not catalog these pages, you would need to know the exact link to access a website in this area of the internet. This could include government services to access your records, health care services, members-only areas, intranets, or corporate resources. A reliable VPN encrypts your traffic before it enters the Tor network, preventing surveillance from your ISP or malicious actors.
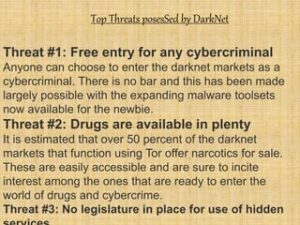
And then there’s malware—click the wrong link or download the wrong file, and your device could get infected. Others are looking for stolen data, hacking services, or even banned books and political content. For sellers, it’s often about making money while staying off the radar. As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data.
Frequently Asked Questions (FAQs) About The Top 10 Dark Web Search Engines
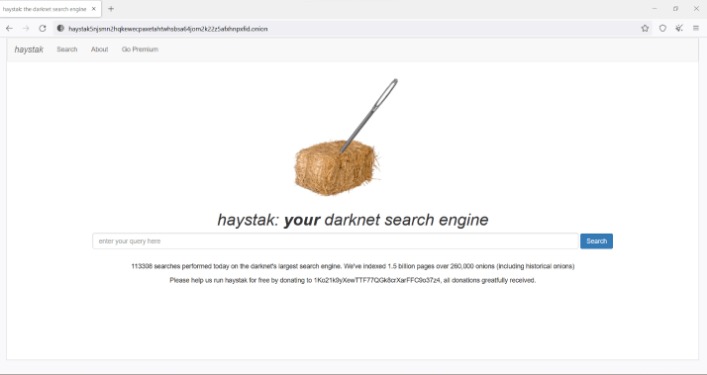
In “safer” mode, JavaScript is disabled on HTTP sites, some fonts are disabled, and all audio and video won’t run automatically, you’ll have to click to play. Slide up to the “safest” level, and as well as those settings, JavaScript is disabled on all sites. With tools like Cyble Vision, it helps organizations stay protected of cyber threats, including dark web monitoring, providing critical insights for better cybersecurity management. DeepSearch is an open-source search engine designed for exploring the dark web within the Tor network. Haystak is a dark web browser that offers better filtering features that help users refine their search results, enabling them to locate exactly what they need. With its minimalist design, WormWeb aims to streamline the dark web experience, making it more accessible for users seeking a straightforward browsing experience.

Navigating The Dark Web Safely

Some are looking for illegal stuff they can’t buy elsewhere, like drugs or counterfeit documents. The second category consists of data stores, which specialize in stolen information. However, just like The Hidden Wiki, consider the links hosted there suspicious. While everything looks above board, there is no knowing if you’re heading to a phishing site, ready to steal your credentials, crypto, or otherwise.
Is DuckDuckGo A True Dark Web Search Engine?
Pitch is a dark web-based Twitter/X alternative, providing a secure platform for anonymous discussions and information sharing. Unlike many dark web platforms, it maintains strict content guidelines while protecting user privacy. TorBook aims to be a privacy-focused alternative to mainstream social networks.
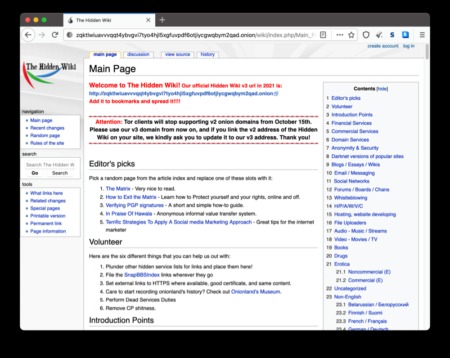
Riseup’s services can be accessed on the surface web or via Tor websites if users want to protect their anonymity. The Hidden Wiki is the dark web’s unofficial Wikipedia, where you can find “.onion” links for many dark web pages, services, and other content. The Hidden Wiki doesn’t discriminate, so if you randomly start diving into the onion sites listed, you may come across objectionable or dangerous material.
Best Dark Web Websites: Video
This random path is called a Tor circuit, and is 3 nodes long by convention, with an entry node (also known described as a guard), a middle node, and an exit node. Tor offers a solution to this problem by anonymizing your traffic as you browse the web with the help of a distributed, anonymous network. This network, known as the Tor network, is a series of volunteer-run routers, or relays, that can talk to each other (as well as normal devices on the internet).
As you might expect, Bitcoin is the top cryptocurrency being used on the Dark Web. Chainalysis says that $790 million worth of cryptocurrencies were used to shop in darknet markets during 2019. While some studies have claimed that illegal Bitcoin activity is as high as 44%.
Step 4: Start Searching onion Websites
The exit node – where your traffic leaves the Tor network and goes to its final destination – is another point of vulnerability. If you’re not using an encrypted communication protocol (e.g. using HTTP instead of HTTPS), this can allow a snooper to intercept and read personally-identifying data in the route’s final leg. When you think of the dark web, you might think of hackers, the Silk Road, and other illegal services that operate covertly and mysteriously. However, the essence of the dark web – anonymous communication – is useful for more than just illicit behavior.
The same anonymity that publishers enjoy on the dark web can be utilized by users who want to read the available information. Again, people who live in countries where the freedom of the internet is limited, for example in China, can really benefit from using Tor. Later on, the underlying Tor code was released into the wild under a free license, leading to the formation of the Tor Project.
This means the Tor Browser is not recommended for streaming video, playing games, or downloading large files. Many dark web search engines are available, and no single option is objectively the best. SecureDrop is designed explicitly for journalists trying to preserve the privacy of their sources. Its anonymous nature enables users to create and submit encrypted documents, chat securely, and receive private responses from journalists.
How Does The Tor Browser Work?
When the final layer of the “onion” is reached and decrypted, the message arrives at its destination. Yes, you can access the dark web on mobile — you just need the right app. Android users need to download the Tor Browser app, while iPhone fans should get the Onion Browser app. Users can ask questions, share answers, and engage in discussions without revealing their identities.