Use Tor Browser, a reliable VPN, and never use your real identity or login credentials. Yes, using a VPN along with the Tor browser enhances your anonymity and security. Known for its massive index and premium version, Haystak is favored by cybersecurity professionals and threat analysts for its depth. Cybercriminals often leverage the anonymity to leak sensitive information, like stolen credentials, credit card numbers, or company data.

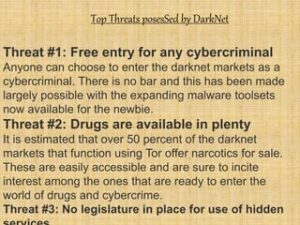
Illicit Activities On The Dark Web
If the VPN connection fails, the automatic kill switch will kick in, temporarily breaking your traffic. The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers. ActiveX and Java frameworks are susceptible to being exploited by hackers.
Illegal Markets
Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. However, there are plenty of legal and legitimate online activities that require privacy and anonymity. The dark web is used by journalists, whistleblowers, and political activists who need the protections that it offers.

Is It Illegal To Use The Tor Browser?
In this article, we’ll take a look at how these tools work, how they differ from traditional search engines, and which dark web search engines are most widely used today. The dark web is an unknown hidden part of the internet that cannot be accessed with default browsers. It can be accessed using specialized software and allows users to hide.
This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites. Formerly known as Archive.is, it is one of the best onion sites on the dark web. It aims to preserve the internet’s scientific and cultural heritage. Unfortunately, it requires you to have an invitation code to create an account. This means you have to know someone who is already using the platform.

The Best Dark Web Search Engines In 2025
Equally important is establishing an efficient workflow to avoid being overwhelmed by the sheer volume of information. Join millions of users who trust ForestVPN for privacy and unrestricted internet access. While TOR anonymizes your activity, using a VPN adds an extra layer of protection by encrypting your connection before it enters the TOR network.

Torch: One Of The Oldest Dark Web Search Engines
It is the part where we use search engines like Google and includes all the indexed websites and pages. The Directory of Open Access Journals is a deep internet search engine that provides access to academic papers. We try our best to filter out onion sites that container CP and other extremly illegal activities. With tools like Cyble Vision, it helps organizations stay protected of cyber threats, including dark web monitoring, providing critical insights for better cybersecurity management. With its minimalist design, WormWeb aims to streamline the dark web experience, making it more accessible for users seeking a straightforward browsing experience. Operating through Tor, DuckDuckGo provides a non-censored search engine experience without logging personal data.
What Is The Dark Web? How To Access It And What You’ll Find

It uses TrustedServer technology on the entire server network to wipe out your data after every session. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. Some of the deep web sites do not use standard top-level domains (TLD) such as .gov, .com, .net, etc. It works by sending internet traffic through volunteer-operated nodes all over the world.
Moreover, when accessing the dark web, you’re probably already looking for things which are either illegal, or restricted by the govt. Designed to cater to both experienced users and novices, Torch’s interface is simple and straightforward. Even if you are new to the darknet, you can easily navigate through Torch and find the information you are looking for without feeling overwhelmed or confused. With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with. Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place.
Deep Web Radio
Anything you need to do that has to be off the books to some extent, for noble or ignoble reasons, can be done on the dark web. Avast SecureLine VPN hides your IP, secures your Wi-Fi connection, and encrypts your data to help protect the information you share and view online. That approach has resulted in Kilos becoming one of the premiere black market search engines, but it’s also why it’s a dangerous portal to a landscape teeming with potential threats. The Kilos search engine is primarily used to find and access dark web markets where illicit drug transactions are one of the main activities.
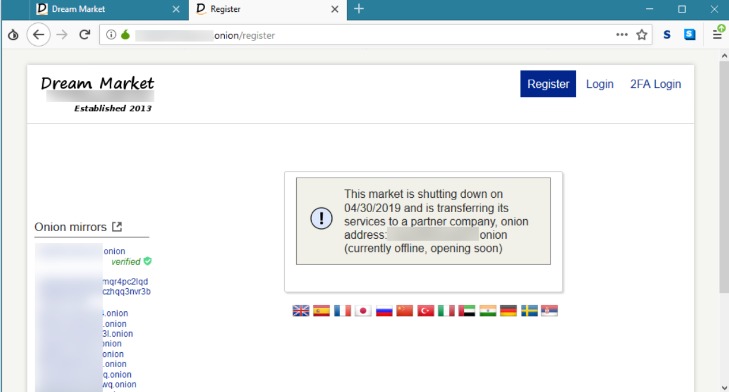
The Hidden Wiki
You’ve probably heard of the “dark web” and wondered what exactly it is and how people navigate its hidden corners. Simply put, the dark web is a part of the internet that’s intentionally hidden from conventional search engines like Google or Bing, meaning it’s inaccessible through typical browsers. People often turn to the dark web for privacy or to access information not available elsewhere, ranging from anonymous forums to censored content or specialized marketplaces. Torch is a dedicated search engine built specifically for the TOR network, indexing .onion domains and hidden services that are inaccessible via traditional web browsers. Launched in 2012, Torch has evolved into a robust, uncensored search platform for Dark Web content, boasting over a million indexed .onion pages.
- With the above dangers, it’s imperative to tread carefully as you step into the dark web.
- If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites.
- This service helps protect your primary email when signing up for .onion services.
- This simplifies the ability to pivot between deep, dark, and surface web sources.
- From drugs and digital goods to hacking tools and counterfeit items, Grams categorizes its search results to help users navigate the vast and diverse darknet landscape more efficiently.
- Flare monitors thousands of channels across sources as diverse as Telegram, the dark web and I2P.
ThreatMon’s Deep/dark web monitoring service provides proactive identification and monitoring of compromised corporate data, sensitive information, or credentials on the dark web. Threat Intelligence roams the dark web, analyzes criminal activity, and gathers clues for its purpose. It monitors dark web forums and marketplaces related and monitors postings.
E.g. some sharing conspiracy theories, personal projects/diaries, or even anonymous social networks. If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet. However, it’s much harder to get at the people who are doing the uploading and downloading. Open up Tor, and you won’t suddenly see the dark web staring back at you.