
The useful site allows you to see how a website looked at an earlier date. This lets you check what information it contained at a previous point in time. This onion site was created as a place for whistleblowers to pass information to journalists. It is a safe haven where anybody with information can share it anonymously and without fear of being tracked.
Torch Search Engine
Like any other site of such nature, Awazon Market isn’t free from risks, so be careful while accessing it. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. Make Tech Easier provides tech tutorials, reviews, tips and tricks to help you navigate the complicated world of technology. Qubes is a leading Linux-based operating system, well known for privacy. Apart from Tails OS, Qubes allows the highest secure connectivity for virtual machine systems. As you can imagine, the dark web has some forums filled with the types of characters who are best avoided.

Why Use Forest VPN With Tor?
For all these reasons, at PrivacyRadar, we strongly discourage using Awazon or any other dark web marketplaces. It’s for the good that these sites are not available for the general internet user. OnionLinks is a library of dark web links, most importantly, active links. Depending on your preference, you can find links in well-categorized groups. These categories include email providers, news sites, privacy, and commercial services.
Additionally, lawful individuals who value their privacy use the dark web to protect their personal information from surveillance and data breaches. Not Evil is a reflection of what the community is looking for and what the community reports as abusive or inappropriate content. We’re back with another video in our Webz Insider video series on everything web data. Learn how to automate financial risk reports using AI and news data with this guide for product managers, featuring tools from Webz.io and OpenAI.
FAQs About Dark Web Search Engines
The only difference is that it passes your traffic through random nodes before reaching the destination. This means your activities cannot be traced or your browser history exposed. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa. You only need to upload your PGP key or let the platform create one.
D List Of 12 Onion Websites
The BBC, among others, is blocked in countries like North Korea or China because of the government’s strict censorship policies. The BBC Tor Mirror is a dark web site that provides uncensored news access. The dark web hosts a variety of content, ranging from legitimate resources like educational materials and privacy tools to illegal activities and scams. Still, since they exist within the dark web, there is a high chance that malicious entities have co-opted one or more for illegal activities. Thus, staying connected to a VPN when you access these sites is vital. Since you cannot access a library of dark web links using the regular Internet, you can check out platforms dedicated to indexing these sites, like The Hidden Wiki.
The internet’s favorite alternative to Google made a name for itself by not logging your search activity yet still providing decent results. This focus on privacy makes it the Tor Browser’s default search engine and one of the best onion search engines. The three nodes separate your IP address from your destination and enable two individuals to communicate without either party, or any middleman, knowing who the other is.

How To Access Onion Sites
If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks.
Mega Market
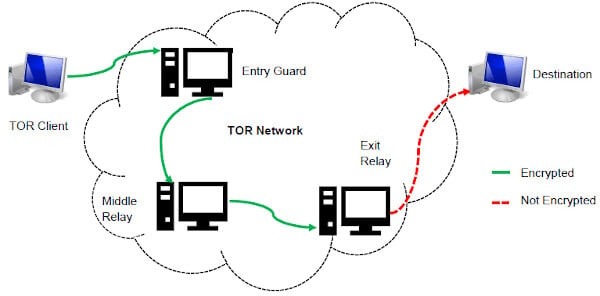
It’s a bit of a contradiction to talk about search engines for dark web sites because, by definition, these are not sites that get indexed by traditional search engines. Many dark web search engines on the darknet suffer from spam, because these spammy sites want to be indexed and found by the search engines as opposed to genuine onion sites. Vorm Web focuses on quality over quantity and splits findable results into three security categories, from secure to risky. You can access onion sites only through the Tor browser or special network configurations. On the Tor network, the onion domain name reflects the fact that, like the layers of an onion, the Tor browser consists of layers of protection. Tor encrypts traffic, masks your IP address, blocks trackers and browser fingerprinting, and doesn’t store a record of your activity.
- Enable MFA wherever possible to protect your accounts from unauthorized access.
- From drug trafficking to arms deals to stolen data, the dark web provides a marketplace for many illegal goods and services.
- The Tor Browser can take you to all kinds of questionable, dangerous, and potentially illegal content.
- The name “onion” comes from the layered structure of the encryption, similar to the layers of an actual onion.
History Of Dark Web Marketplaces
This site supports PGP encryption and two-factor authentication features. DarkFox Market is the largest dark web shop selling various products and attracting more vendors and users. It is a wallet-based shop, meaning you must first deposit bitcoins into your wallet before purchasing any goods and services. The marketplace is much more organized, which makes it easy to use and navigate. Accessing any darknet marketplace is dangerous because it is known to be a hub for illegal trade.
- Because of their anonymity, dark web sites are breeding grounds for illegal activity and transactions.
- Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools.
- Malicious hackers on the dark web use various advanced techniques to perform cyber attacks, security breaches, and compromise data.
- Some services are genuine; you can get what you want at an agreed fee.
Don’t Stick Your Nose Where It Doesn’t Belong
She holds a Bachelor’s degree in Liberal Arts and a triple Master’s degree in Literary and Cultural Studies. Outside of work, she is a travel enthusiast, music lover and avid learner interested in global cultures, spirituality, psychology and neuroscience. The dark web is part of the hidden web, which comprises non-indexed websites that are mostly used for illegal and illicit activity. If you have heard your peers or colleagues throw this term around and are wondering, “What is the dark web? SecureDrop is an open-source whistleblower submission system that news organizations can install to receive documents and tips from sources safely (and anonymously).

He has worked for several international tech platforms, and his writing and editing expertise has also enhanced over time. He loves covering topics about VPNs, online privacy, and anonymity and shares his knowledge of online security with internet users through his words. This browser is the most suitable option for accessing the dark web, thanks to its multiple layers of encryption. Each time you connect to a dark web link, your request and traffic are routed through at least three different server points, ensuring your IP remains hidden. Hence, even if you hide your IP address, you aren’t completely secure.



