As for Tor and other anonymous browsers that allow access to the Deep Web and the Dark Web, using them isn’t illegal in most countries. However, anonymous browsers are banned in China, while Russia and some other countries actively block their citizens from using them. Yes, the Dark Web exists as a small subset of the Deep Web — part of the internet that isn’t indexed by search engines and thus isn’t publicly available. Experts estimate that the Dark Web accounts for no more than 5% of the entire internet. While stolen accounts across other categories saw year-over-year price drops, Deep Web facts reveal that crypto was up from 2022. That’s because digital currencies went stagnant between Q3 of 2022 and Q1 of 2023, resulting in less interest in buying crypto during this period.
Top 7 Dark Web Marketplaces

Genesis Market extensively used a payment processor called UAPS, so much that the processor’s average inflows fell by 25.7% after Genesis closed last April. Regardless, UAPS remains a key provider of payment infrastructure to top fraud shops. In one particularly devastating case, a man lost his entire $80,000 pension.
As long as data is routinely stolen, there are likely to be marketplaces for the stolen information. In total, there were 2,158 vendors who advertised at least one of the 96,672 product listings across the 30 marketplaces. Vendors and product listings were not distributed equally across markets. On average, marketplaces had 109 unique vendor aliases and 3,222 product listings related to stolen data products. Marketplaces recorded 632,207 sales across these markets, which generated $140,337,999 in total revenue. On average, marketplaces had 26,342 sales and generated $5,847,417 in revenue.

How To Protect Your Identity While Browsing The Dark Web
In fact, previous studies on DWM transaction networks have revealed crucial aspects of the ecosystem13,14,15. However, they have so far mainly focused on DWM users, without distinguishing between buyers and sellers, and neglecting the different weight that more active users may have in the system. The reason is that the operational structure of DWMs inherently hides the seller–buyer link, as all transactions are made through the marketplace. Buyers send money to the marketplace, which in turn sends the money to the seller. Vendors on Hydra also offered services such as “Hacking for Hire,” “Ransomware as a Service” (“RaaS”), and a myriad of money laundering features.
Germans Accounted For 5256% Of Tor’s Direct Daily Users In Q3 Of 2023
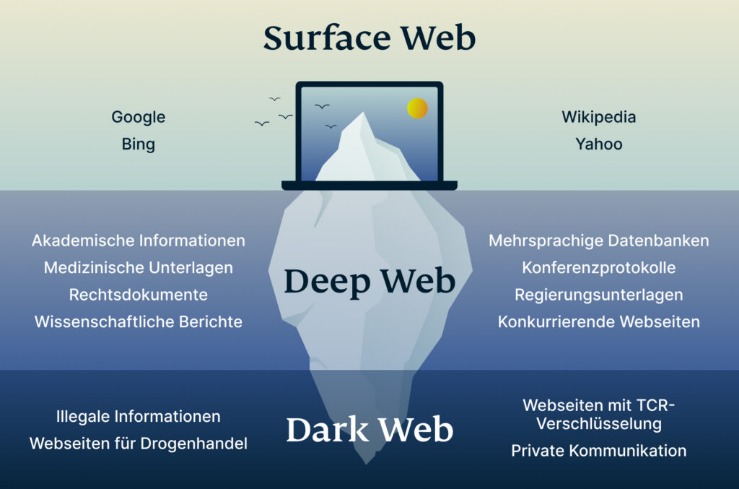
It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web.
Explicit Content
Over time, ambitious individuals created infrastructure for these transactions, where for a fee, sellers have access to a digital ‘storefront’ to sell their products in a centralized marketplace. The stolen data supply chain begins with producers—hackers who exploit vulnerable systems and steal sensitive information such as credit card numbers, bank account information, and Social Security numbers. Next, the stolen data is advertised by wholesalers and distributors who sell the data. Finally, the data is purchased by consumers who use it to commit various forms of fraud, including fraudulent credit card transactions, identity theft, and phishing attacks. Darknets and dark markets have fueled the growth of cybercrime, provided a marketplace for cyber threats, and expanded the attack surface for malicious actors. Dark web search engines support dark web marketplaces and allow users to use them, but still accessing them is full of risks; they can infect your device with malware or viruses, and can bring other legal consequences.

Where Funds Go After Leaving Darknet Markets
Established in 2012, the platform is a time capsule that collects snapshots of websites. These onion addresses will remain online even if the original page disappears. It also keeps the graphical copy and text of the page for better accuracy.
Darknet Markets Generate Millions In Revenue Selling Stolen Personal Data
- In this era, it takes one wrong click and all your sensitive data ends up in the wrong hands.
- Our analysts will continue to follow this market’s presence and reputation on the darknet, and provide further updates as this story unfolds.
- This malware-as-a-service model allows less tech-savvy criminals to launch malware-driven cyberattacks without building the tools themselves.
- Therefore, it means that even the guns on the dark web start legally, but along the way from creation to purchasing, a lot of things happen, which makes it easier for the guns to end up on the dark market.
- Using a dark web search engine is a great step towards enjoying a more secure experience while shopping on the platform.
Looking a step further, DarkOwl analysts reviewed one of the products. The below screenshot is one of the above products and advertises as, “Pre-Shredded Cash 25,000 USD Cash” and is for sale for $999.00, which was discounted from an original price of $2,100.00 USD. The vendor claims these US dollars came from the Federal Reserve in 2017. The vendor self identifies as “The Queens Cash aka queencdcguev” in the below description. Counterfeit goods are products that are made to imitate genuine items with the intention of deceiving others.
The structural change in the multiseller network and the resilience of the multibuyer network. Temporal network of multisellers (top) and multibuyers (bottom) between markets for each year. Edges are multihomers, i.e., traders that are simultaneously active in both markets (sellers in the multiseller network, and buyers in the multibuyer network). The width of the edges is proportional to the number of multihomers acting between the markets. With the advent of several markets at the beginning of 2014, the number of multisellers rapidly grows, representing more than 20% of all sellers until the beginning of 2016 (see Supplementary Information Section S3).

One of the most well-known technologies enabling darknets is the Tor network, which was developed by the U.S. Naval Research Laboratory in the mid-1990s and later released to the public. Tor, short for “The Onion Router,” routes internet traffic through a global network of volunteer-operated servers to anonymize a user’s online activity. This technology initially had noble intentions, aiming to protect activists, whistleblowers, and individuals in repressive regimes.

Awazon Market is a top-tier dark web marketplace with claims to revolutionize secure anonymous commerce. It offers a wide range of goods and services with robust anti-DDoS protection (with military-grade security protocols) and no JavaScript, ensuring privacy and uptime. This guide outlines different ways of safely accessing dark web stores and the list of reliable dark web marketplaces you can consider visiting in 2025 for research and monitoring purposes. Dark Empire Market appears to have originally surfaced in early 2021, based on the earliest results that are still viewable on the site. However, its popularity increased shortly after the Bohemia, Hydra, and Monopoly markets were seized in early 2023.
It supports operations in multiple languages and operates on both clearnet and Tor. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data. It has a bidding feature, with new batches of stolen data being frequently added. The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown. One of the most common is the exit scam, where a marketplace suddenly disappears and takes everyone’s money with it. There’s also a privacy angle—some users live in countries with censorship or surveillance, and the dark web gives them a space to communicate or access information more freely.